For original article click here.
Stack Identity recently released the industry’s first Shadow Access Impact Report that shared key findings of how cloud data breaches are enabled by identity and access control gaps, and how existing IAM tools are not designed to address the problem.
What is Shadow Access?
Shadow Access is unauthorized, unmonitored and invisible access to cloud environments that is inadvertently created by normal cloud operations. In the cloud, new identities and entitlements are being automatically created to connect cloud services with data and applications across systems. To streamline processes and optimize automation in the cloud, the related identities and entitlements are often overly permissioned.
![]()
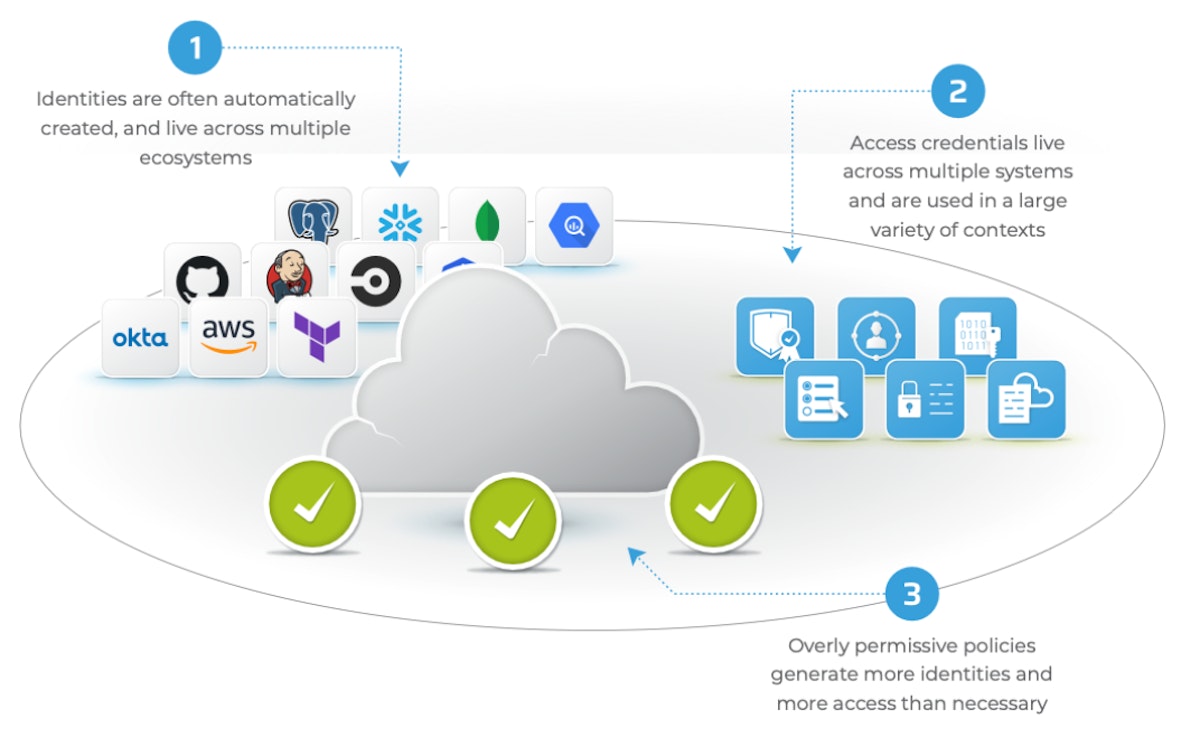 What is Shadow Access
What is Shadow Access
At the same time, due to the automation aspect of cloud operations, there is little to no oversight, especially since existing IAM tools are not able to capture and keep pace with the pace of change in the cloud. This results in extremely limited visibility and ability for security teams to ensure governance and compliance.
Security, compliance and governance are adversely impacted by Shadow Access
Compliance and governance processes cannot keep pace with the rate of change of IAM in the cloud. Existing tools and processes to manage access compliance in the cloud are time-consuming, resource intensive and static, with compliance teams relying on disparate tools such as screenshots and spreadsheets. In fact, Cloud IAM data is distributed across many tools including Cloud IAM, Cloud IDP, Infrastructure as Code, data stores and HR systems. And governance of access is scattered across ticketing systems, emails, spreadsheets and screenshots. Existing tools don’t see Shadow Access visibility as a huge problem, which results in IAM blindspots and creates security, compliance and governance problems.
![]()
 Shadow Access Impact
Shadow Access Impact
Shadow Access causes dangerous cloud data breaches
Gaps in cloud security, due to the IAM blindspots created by Shadow Access result in significant cloud data breaches. The report highlights how one attacker replaced a Lambda function with malicious code that added an IAM user in order for an unauthorized entity to infiltrate the cloud environment. In another real world example, an attacker leveraged programmatic access created for an external vendor, and from there, infiltrated the cloud environment, resulting in S3 being used for crypto mining and malware hosting. In yet another instance, the AWS policy console simply did not (and does not) show effective permissions or inherited permissions to an identity or resource enabling invisible access by an attacker.
How to address the problem of Shadow Access and regain control of compliance, governance and security in the cloud
All the aforementioned cloud data breaches were results of IAM blindspots created by Shadow Access. To remediate the problem, three steps are needed:
- Gaining visibility of the fragmented cloud IAM data is the first step in solving the problem of Shadow Access. Once there is a comprehensive view of IAM data, detections can extract insights from the data to implement various technology use cases supporting CIEM, DSPM, and Cloud IGA.
- Detections can then use the comprehensive data to answer the question ”What are the pathways by which the cloud environment can be breached, and how can data be exfiltrated?”
- Finally, with visibility and detection, it is possible to predict the likelihood of data breaches, data exfiltration, and ransomware attacks targeted at cloud data. Without a comprehensive view of cloud IAM data, accessing audits and ensuring compliance becomes painful, expensive and often unpredictable.
Identity is a security vector where enterprises can have complete control and therefore understanding of the problem of Shadow Access, which enables the most impactful remediation of one of the largest security risks in cloud environments. Gaining visibility of Shadow Access is the key to containing the chaos created by Shadow Access and getting security, compliance and governance back on track and reducing the risks of cloud data breaches and data exfiltration.
Readers can learn more about Shadow Access, the impact on DevOps, SecOps and how to address the problem by downloading the full report here: https://stackidentity.com/the-shadow-access-impact-report/.
To run an assessment of Shadow Access vulnerabilities and find the IAM blindspots in your cloud environment, register here: www.stackidentity.com/Shadow-Access-Risk-Assessment.
